Spyware Can Result In All The Following Except
Arias News
Mar 29, 2025 · 5 min read
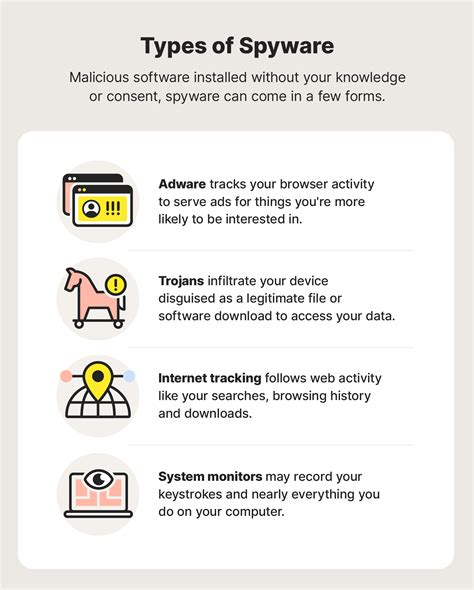
Table of Contents
Spyware Can Result in All of the Following Except… What?
Spyware is a pervasive threat in today's digital landscape, silently infiltrating devices and stealing sensitive information. Understanding its capabilities is crucial for protecting yourself and your data. This comprehensive guide explores the various harmful effects of spyware, pinpointing the one outcome it cannot directly cause.
The Deceptive World of Spyware: Understanding its Reach
Spyware, short for "spy software," is malicious software designed to monitor and collect information from a user's device without their knowledge or consent. This data can include anything from browsing history and keystrokes to location data and financial information. The insidious nature of spyware lies in its ability to operate covertly, often leaving users completely unaware of its presence.
How Spyware Infects Devices: The Common Pathways
Spyware employs various methods to infiltrate devices, including:
- Malicious Downloads: Downloading infected files or software from untrusted sources is a primary infection vector. This includes seemingly legitimate software cracked or downloaded from unofficial websites.
- Phishing Emails: Deceptive emails containing malicious attachments or links leading to spyware-laden websites are a common tactic. These often mimic legitimate communications from banks or other trusted entities.
- Drive-by Downloads: Simply visiting a compromised website can trigger a drive-by download, automatically installing spyware without the user's explicit action. This frequently happens on websites with poor security practices.
- Software Vulnerabilities: Exploiting vulnerabilities in software, operating systems, or web browsers allows spyware to gain access to a device. Keeping software updated is crucial to mitigate this risk.
- Bundled Software: Spyware can be bundled with legitimate software, often during the installation process. Users might unknowingly agree to install spyware alongside a desired program.
The Detrimental Effects of Spyware: A Comprehensive List
The consequences of a spyware infection can be severe, impacting both personal privacy and financial security. These include:
1. Data Theft: The Core Functionality of Spyware
This is the primary goal of most spyware. Stolen data can include:
- Personal Information: Names, addresses, phone numbers, email addresses, and social security numbers are highly valuable to identity thieves.
- Financial Data: Banking details, credit card information, and online payment credentials are prime targets for financial fraud.
- Passwords and Login Credentials: Access to online accounts, emails, and social media profiles allows criminals to take control of various aspects of a victim's life.
- Sensitive Documents: Private files, such as medical records, tax documents, and legal agreements, can be stolen and used for malicious purposes.
- Photos and Videos: Personal photos and videos can be stolen and used for blackmail or distributed online without consent.
2. System Slowdown and Instability: The Performance Impact
Spyware consumes system resources, leading to:
- Slower Processing Speeds: The constant monitoring and data transmission activities of spyware strain the device's processor, resulting in sluggish performance.
- Frequent Crashes and Freezes: The excessive resource consumption can lead to system instability, causing frequent crashes and freezes.
- Increased Boot Times: The spyware might start running before the operating system fully loads, slowing down the boot process.
3. Identity Theft and Financial Fraud: The Serious Consequences
The stolen data is used to commit:
- Identity Theft: Criminals can use stolen personal information to open fraudulent accounts, apply for loans, or commit other crimes in the victim's name.
- Financial Fraud: Stolen financial information is used for unauthorized transactions, leading to significant financial losses.
- Account Takeovers: Access to online accounts allows criminals to take control of emails, social media, and online banking accounts.
4. Monitoring and Tracking: The Loss of Privacy
Spyware constantly monitors user activity, compromising privacy by:
- Tracking Browsing History: Spyware monitors websites visited, revealing browsing habits and interests.
- Monitoring Keystrokes (Keylogging): This records every key pressed, allowing criminals to capture passwords, credit card numbers, and other sensitive information.
- Tracking Location Data (GPS Tracking): Spyware can track the device's location using GPS, revealing movements and whereabouts.
- Recording Conversations (Microphone Monitoring): Some advanced spyware can activate the microphone to record conversations.
5. Ransomware Attacks: The Extortion Tactic
While not always directly caused by spyware itself, spyware can facilitate ransomware attacks by:
- Providing Initial Access: Spyware can create a backdoor, allowing ransomware to be installed easily.
- Mapping Network Infrastructure: Spyware can map the network to determine valuable assets that ransomware can encrypt.
What Spyware CANNOT Directly Cause: The Exception
While spyware's capabilities are extensive and damaging, there's one thing it cannot directly cause: Hardware Failure.
While spyware can certainly contribute to hardware failure indirectly – through excessive resource consumption leading to overheating, for example – it doesn't directly cause the physical breakdown of hardware components. Hardware failure is typically caused by physical damage, wear and tear, manufacturing defects, or power surges. Spyware's impact is purely software-based. It can degrade performance and stability, but it won't physically break your hard drive or damage your RAM.
Protecting Yourself from Spyware: Essential Precautions
Protecting your devices from spyware requires a proactive approach:
- Install and Maintain Anti-Spyware Software: Regularly update and run reputable anti-spyware programs to detect and remove spyware.
- Practice Safe Browsing Habits: Avoid suspicious websites, download software only from trusted sources, and be cautious of email attachments and links.
- Keep Software Updated: Regularly update your operating system, web browser, and other software to patch security vulnerabilities.
- Use Strong Passwords and Two-Factor Authentication: Protect your online accounts with strong, unique passwords and enable two-factor authentication wherever possible.
- Be Wary of Free Software: Free software often comes bundled with unwanted programs, including spyware. Pay close attention during the installation process.
- Educate Yourself and Others: Stay informed about the latest spyware threats and educate family and friends about safe online practices.
- Regularly Back Up Your Data: Regularly back up your important files to an external hard drive or cloud storage service. This safeguards your data even if your device becomes infected.
- Scan USB Drives Before Use: Always scan external storage devices, such as USB drives, for malware before using them on your computer.
Conclusion: Vigilance is Key in the Fight Against Spyware
Spyware represents a significant threat to both personal privacy and financial security. By understanding its methods, consequences, and limitations, and by implementing strong security measures, you can significantly reduce your risk of infection and protect yourself against its harmful effects. Remember, while spyware can degrade performance and steal your data, it cannot directly cause hardware failure. However, the indirect consequences of a severe spyware infection can significantly shorten the lifespan of your device. Proactive protection is your best defense.
Latest Posts
Latest Posts
-
How Many Bags Are In A Ton Of Wood Pellets
Mar 31, 2025
-
What Is The Greatest Common Factor Of 27 And 45
Mar 31, 2025
-
3 4 Cup Sugar Is How Many Grams
Mar 31, 2025
-
Did Glen Campbell Sing In The Movie Chisum
Mar 31, 2025
-
Only What You Do For Christ Will Last Scripture
Mar 31, 2025
Related Post
Thank you for visiting our website which covers about Spyware Can Result In All The Following Except . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
